If last year taught us anything, it was that we can move quickly to organise a fully online hacker conference in little over a month. This year our annual, internal hacker conference ran from the 16th to the 18th of September, was attended by 102 hackers from 9 countries across 2 timezones, and was once again filled with epic hacks and laughs! In this post I’ll tell you more about the run up and execution of our internal SenseCon 2021! Some of this year’s challenges are available to play for a limited time on our Orange Cyberdefense Hacker Discord server as well. You can join using this link: https://discord.gg/yhfPKyBGbp.
motivation
SenseCon is a unique opportunity for roughly 150 Orange Cyberdefense hackers globally to come together, learn and share with each other. We do this by running challenges, workshops and a hackathon aimed at accelerating research while encouraging collaboration across teams. Everything the conference has to offer is sourced and built by the same community of hackers, which include the trainings, challenges and events.
theme
I’m a fan of the classic 1983 film, Wargames. “Accidentally” hacking into a military mainframe to nearly trigger a global thermonuclear war excited me as a kid. It was a tremendous amount of fun to bring various references from the ionic movie to life almost 40 years later.

No opportunity was wasted to pay homage to this great film as you’d see in the sections that follow.
discord
Last year we organised ourselves via Discord. It worked so well that we didn’t even consider alternatives. Instead, we jumped right into building a fresh bot. We completely embraced Discord this time, integrating every part of the conference experience with it. Whether it was onboarding, running challenges or accepting flags, the bot did it all!

We wrote the bot in TypeScript, leveraging discordjs to access Discord itself. If you’ve never used discordjs before, at a high level, once connected to Discord, events are emitted for various things such as reacting to or posting messages. Once your bot is connected, you can work with incoming messages using the messageCreate event on the client object. For example:
client.on('messageCreate', async message => { const { content, author } = message; // do something with the content, or the author });
After doing some work you can then (optionally) reply to an incoming message with something like await message.reply('hey!');. This was the basic pattern we used for most of the interactions with the bot.
challenges
There were four official challenges, four “easter egg” challenges, three password challenges and one “global” challenge scattered throughout the server.

The official challenges all had a series of flags to be captured that you would submit to the bot using the submit flag (&sf) command. Submitting a valid flag would have you earn a Discord role, signalling that you completed a challenge in a #role-log channel for everyone to see.
There were several contributors of challenges, which included challenges from Cyril (@M4yFly), Ross (@HypnInfoSec), Marianka (@mariankabotes), Marlise (@Lise_p), Szymon (@TH3_GOAT_FARM3R) and myself. Most of the challenges should have dedicated write ups talking about how they were built and intended to be solved coming soon.
the global challenge
As the Wargames movie progresses, General Beringer shifts the current DEF CON level based on the perceived threat level. One of the iconic quotes from the movie is “Shall we play a game?”. This is seen early in the film when David finally authenticates to the WOPR using the password “Joshua”, starting a game of Global Thermonuclear War. (It’s also one of my favourite scenes where David and Jennifer are genuinely having fun playing it). Later in the film we’re brought back to the games menu, but this time David suggests that they play tic-tac-toe (a game not on the WOPR’s game list) to prevent it from launching a real nuclear strike.
We added a mechanic where the DEFCON level changed based on how many games of tic-tac-toe were won either by the bot or the humans in the last hour. Practically, tic-tac-toe could be played in two ways; one by invoking the “game play tictactoe” command (&gp tictactoe), or when the bot randomly sent you a direct message to play a game.
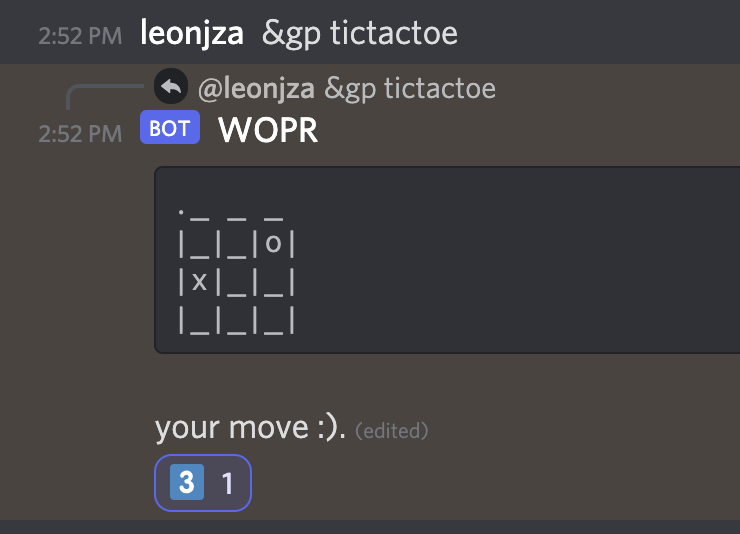
The bot would win in two conditions – either the game times out, or you actually lost as a human. The bot would announce each DEFCON level change in a channel, and when it reached DEFCON level 1, it would start launching nukes, killing members.
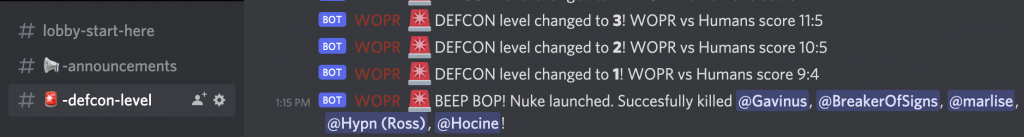
Once killed, you earned a “dead” role. Having this role meant that you could no longer use any challenge commands (ie. commands starting with an &). The only way to come back was to have the human’s score be more than the WOPR score, pushing the DEFCON level back to level 5. At level 5, the bot would concede and “revive” all dead players. This mechanic encouraged some group work to get others to play tictactoe to win again :D
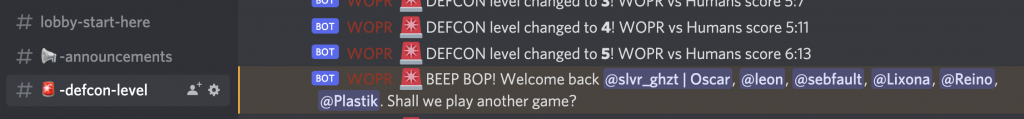
To add some extra flair to the overall DEF CON level, we also updated the server banner to match the colours of the DEF CON levels as they were in the movie.


challenge – war&unity
A challenge contributed by Ross, War&Unity was a Unity game hacking challenge. The game itself was a recreation of the arcade scene where David often played Galaga and NORAD, where the WOPR lived.


While one of the flags is easily available if you dropped the games DLL’s in a reflector like dnSpy, other flags are intentionally not as easy to find. No grep game hacking here!
challenge – pdfmaker
Contributed by Cyril from France, PDFMaker is a web based challenge that was very well received (even by those that were frustrated by it haha!).
This challenge required no brute force, so go ahead and ^c that ffuf session. Instead, the PDF engine was vulnerable to a server-side cross-site scripting attack that allowed you to exfiltrate the applications DLL and reveal the flag. Watch out for some writeups on this one.
challenge – passwords
The password cracking challenge, contributed by Marlise, Marianka and Szymon was composed of three parts. The challenges were called Nist, Http and Jwt, and you could get the hash lists by running the &pd command.
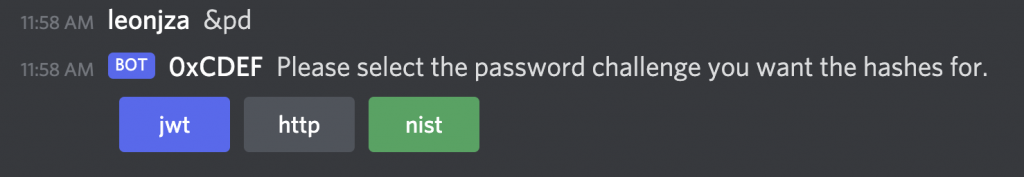
Once you cracked a few, you could upload your clears back to the bot to score points, allowing you to compare with others. There will be blog posts coming soon detailing the challenges themselves so watch out for those!
challenge – global thermonuclear war
A challenge cooked up by myself, Global Thermonuclear War is a two part challenge that you have to solve by interacting with the bot.
When announcing SenseCon internally, I like to build small challenges into the announcement messages. I made this years challenge email public here for you to play with as well. Global Thermonuclear War was a continuation of the same theme used in that challenge.
To start the challenge, you would message the bot >w.w, whereafter it would ask for a “launch code”.
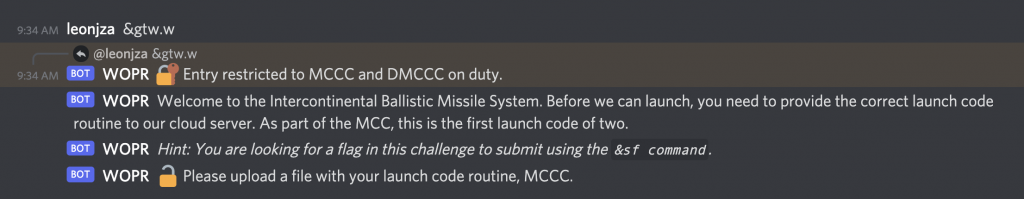
Uploading a file as your “launch code”, you’d be presented with the output of a system “booting” (as in OpenRC doing its thing).
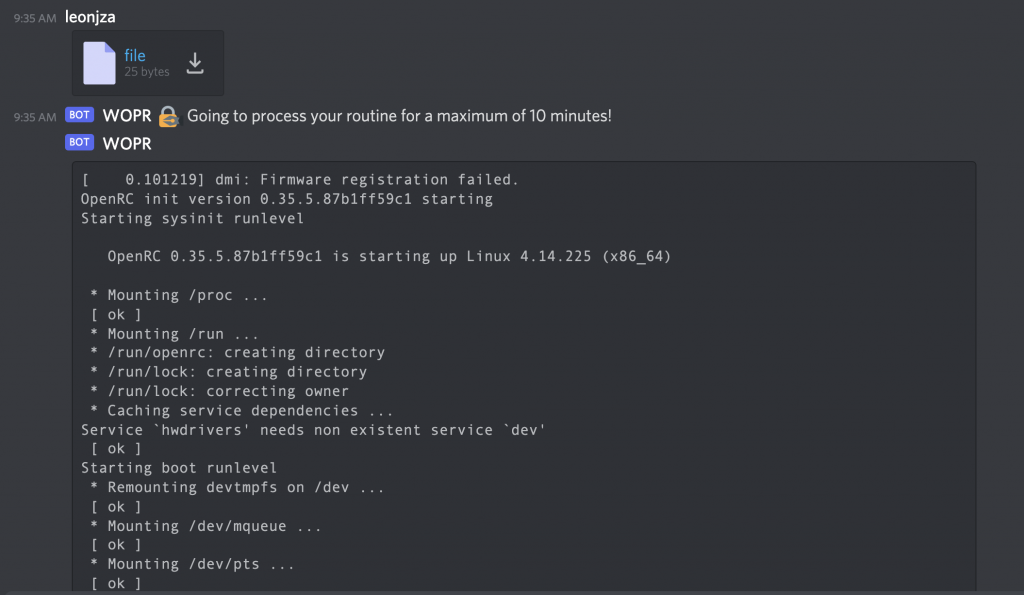
Behind the scenes, a Firecracker MicroVM is booted and the player’s uploaded file mounted in and its console output streamed to Discord.
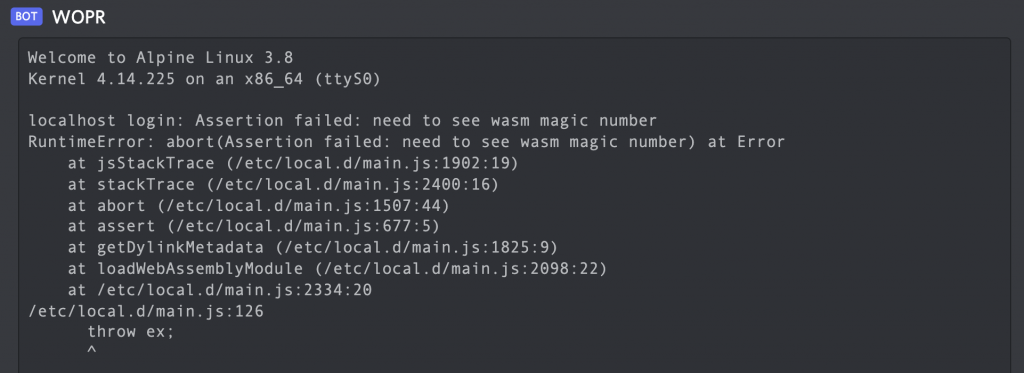
Depending on what you uploaded, the errors would let you figure out what was needed.
Part two followed a similar path, but I’ll save the spoilers for now.
challenges – other
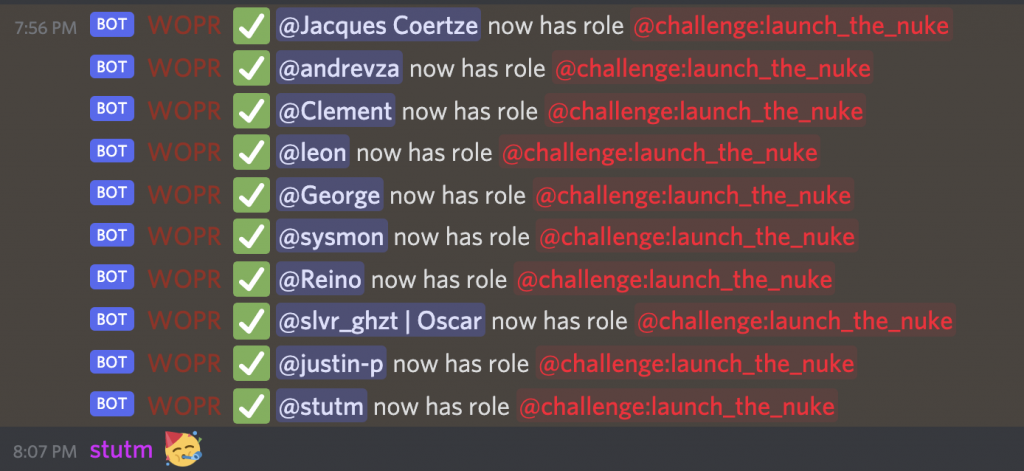
There were many other challenges, as well as several “easter” eggs we built. One specific easter egg challenge was called “launched_the_nuke”, and was given to everyone that sent the launch code CPE1704TKS in a thread, one after the other.
training
A SenseCon wont be a SenseCon without workshops and training! This year we had three workshops delivered by Elias Issa, Yohann Gely and Felipe Molina de la Torre.
Elias delivered a Red Teaming Reconnaissance workshop. The recon phase is arguably one of the most important phases in a multi faceted, multi-discipline red teaming exercise, and in this workshop we went through many practical exercises emphasising just that.
Yohann delivered an introduction to PLC coding workshop. The workshop started with basic PLC development techniques using an online PLC simulator, and later progressed to more advanced techniques with Open PLC editor.
Felipe delivered an Advanced Web Scraping workshop. The workshop aimed to accelerate participants’ abilities to scrape data from web sites beyond the common beautifulsoup python library and regular expression combination and instead focussed on advanced use of scrapy.
hackathon
Without a doubt, the most important event at an internal SenseCon is the hackathon. The idea is to spend 24 hours on a project of your choosing to build or break anything that tickles your fancy. These hackathon projects often evolve into much deeper security research efforts, resulting in DEF CON talks and more! Be sure to keep an eye on the blog as these projects mature.
This year we had 8 teams, working on the following projects:
- Team Facelock: Building a facial recognition daemon that would lock / unlock your computer based on who it recognises.
- Team Fuzzy Daemons: Updating an old USSD fuzzer, porting it to python 3 and adding new features.
- Team Los Pollos Hermanos: EDR investigation focussing on understanding internals of Cylance and Cybereason, testing well known API unhooking methods.
- Team Overwatch: Build an automatic license plate recognition system that alerts if the same car passes your house too often.
- Team pwnbox: Build a dropbox that emphasises passive network information & intelligence gathering.
- Team Rød grød med fløde: Extend project discoverie’s Nuclei templates to include templates that could help speed up and automate repetitive tasks such as checking response headers, cookie flags and more.
- Team Susinternals: Replace impacket’s PSExec implementation leveraging remcom with the Microsoft’s sysinternals version that provides a signed service instead.
- Team The Oracle: A fair amount of security research exists for AWS, Azure and GCP, but who is looking at Oracle Cloud?
evening events
Having an online conference does not mean evenings have to be dull. Instead, we played some games the first evening, had a quizz night the second and had a movie night on the last evening.
you can play too!
We’ve worked hard to prepare a discord server where you can get a chance to taste some of the fun and challenges we had this year. You can join us at the Orange Cyberdefense Hacker community server here: https://discord.gg/yhfPKyBGbp.
conclusion
One blog post simply isn’t enough to tell you about everything that happens at SenseCon, but I hope this gave you a feel for what we get up to. With time, all of the code and challenges should appear on Github, and as the hackathon projects progress, some interesting research should be made available soon!


