Hijacking SSL sessions initiated by the browser is a trivial task. The challenge comes when trying to intercept SSL traffic in applications such as Dropbox or Easynote. These apps create additional measures to verify certificates and their integrity, hence not very friendly to perform with Burp.
One quick solution to the above problem is hiding one level above (or below :) the OSI layer. Live API monitoring // hooking can be used to capture and manipulate HTTP/S “traffic” before it being placed on the wire, more or less the same way are used to doing it in Burp.
One great tool is the Rohitab API Monitor, which allows you to monitor, and control, API calls made by applications and services.
Steps: Attach to a target process in realtime -> selectively monitor/hook its API -> place breakpoints and manipulate API call parameter content at will.
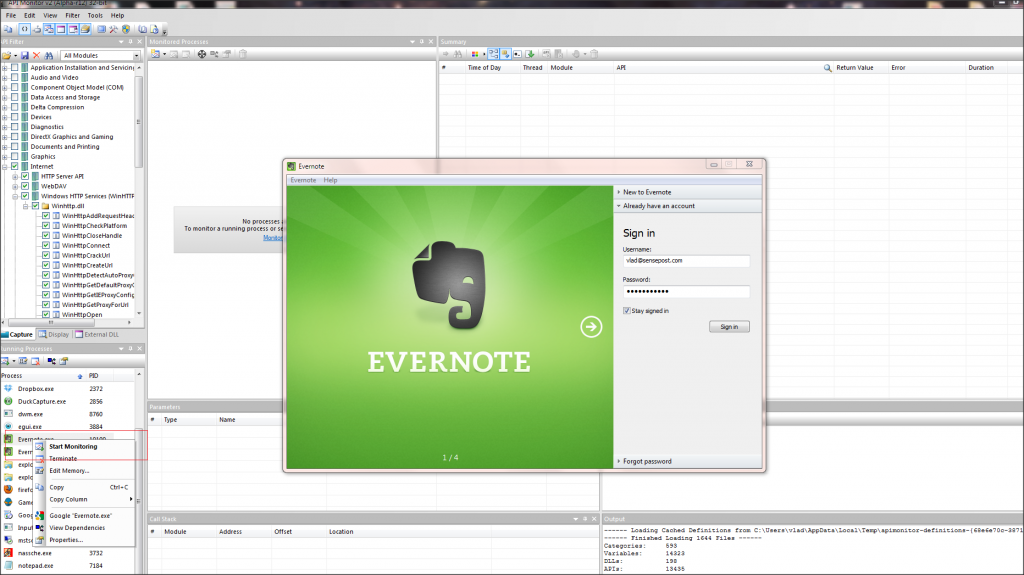
Fig 1 – Attaching to evernote.exe | Selecting Internet (HTTP Srv API, WEbDav, WinNet etc…) API as primary filter for the session.
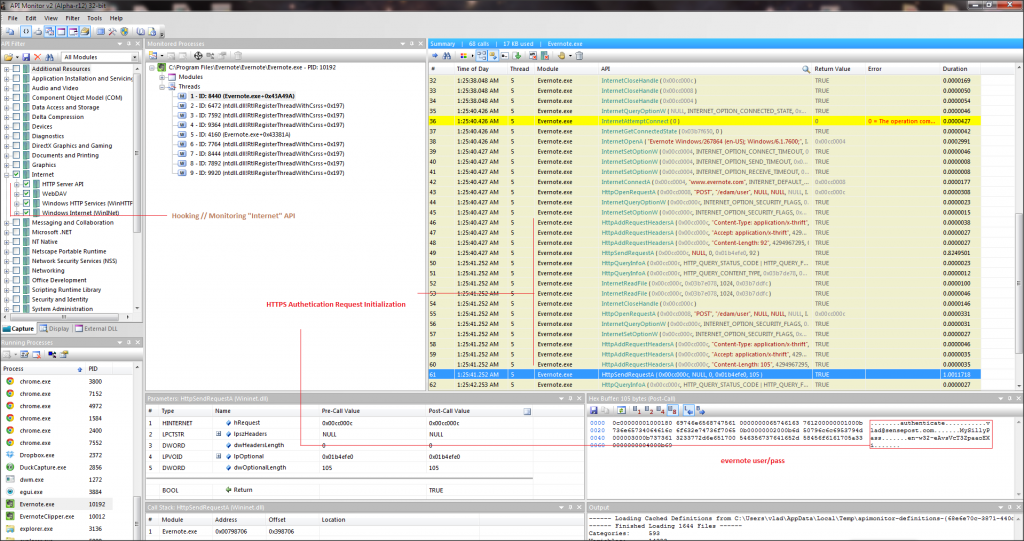
Fig2 – Examining HttpSendRequestA call (contains my easynote creds :) ) in realtime, before the assembled POST request leaves the host.
P.S. That isn’t my password.