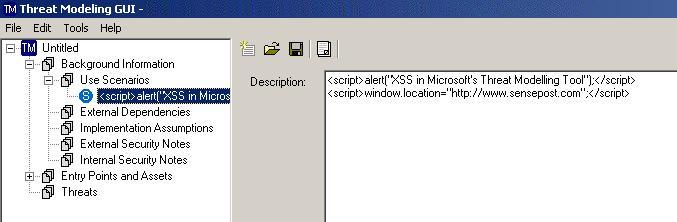
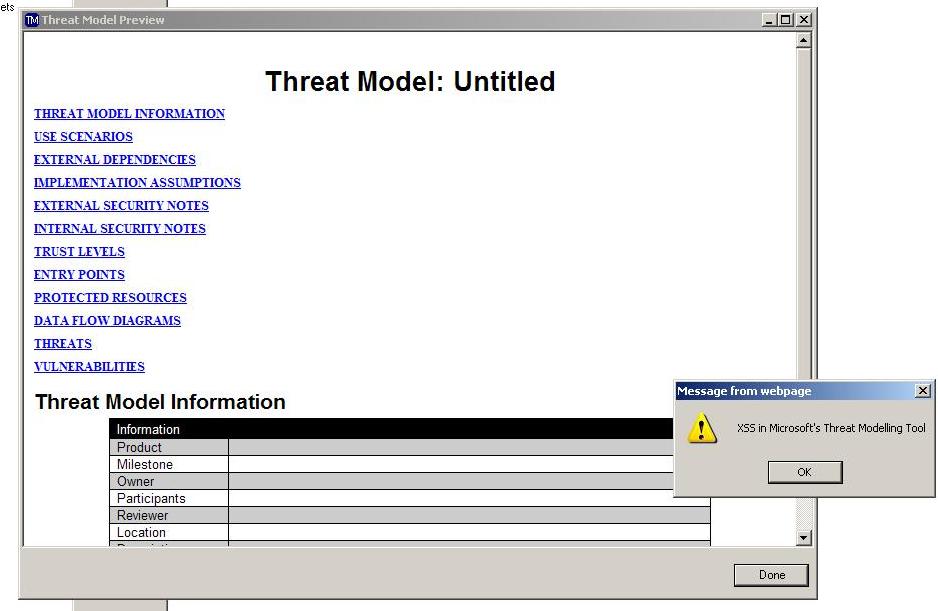
Just arbitrary coolness regarding Microsoft’s Threat Modeller. It’s XSS-ible…
Since this all works in file:///, not overly sure what the benefits of these things will be, but I suppose since different folks may have different privilege levels for different protocol handlers (ie: file:// http:// etc), one might be able to instantiate previously unusable OCX’es, or even redirect to site for exploiting browser vulnerabilities.
Never happened unless there are pictures, so refer below…
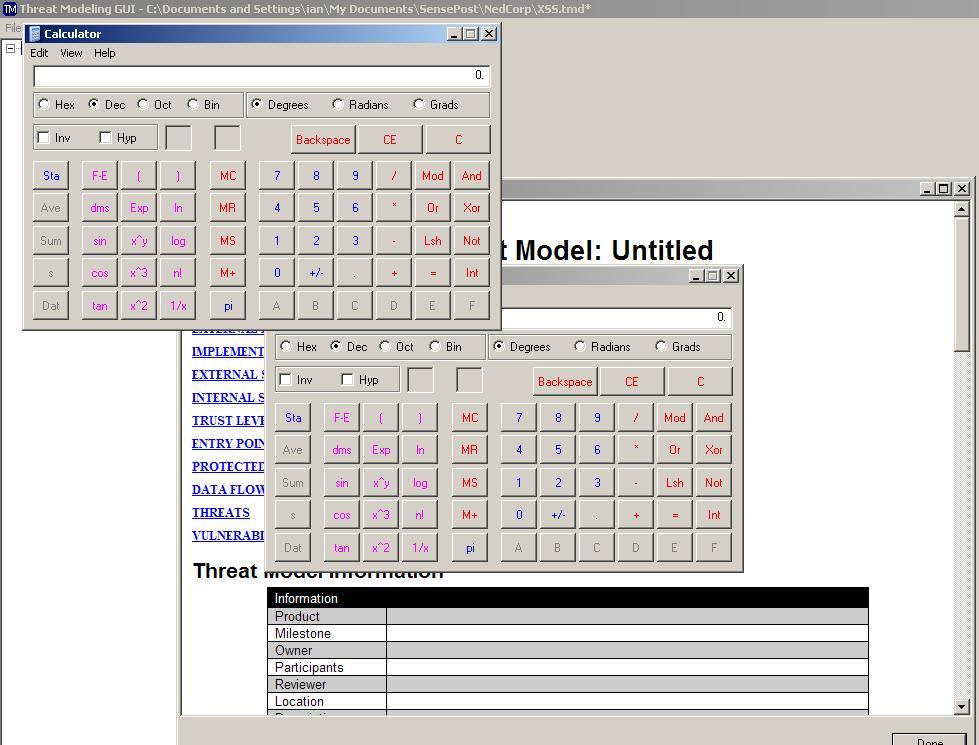
A little further playing, along with some vulnerable ActiveX controls, and we find ourselves with a nice mechanism for getting remote code execution… :)
Finally, a little update. After reporting the issue to secure@microsoft.com, we get a response from Nate mentioning the following:
“Thank you again for bringing this to our attention. Given that this product has been deprecated, the MSRC won’t open a case to investigate the issue. I am however going to contact the Download Center and see if we can get the download removed since new tools/versions are available. If you find the same or other issues in the current version/tool please let us know. If you have any questions or concerns please let me know.”
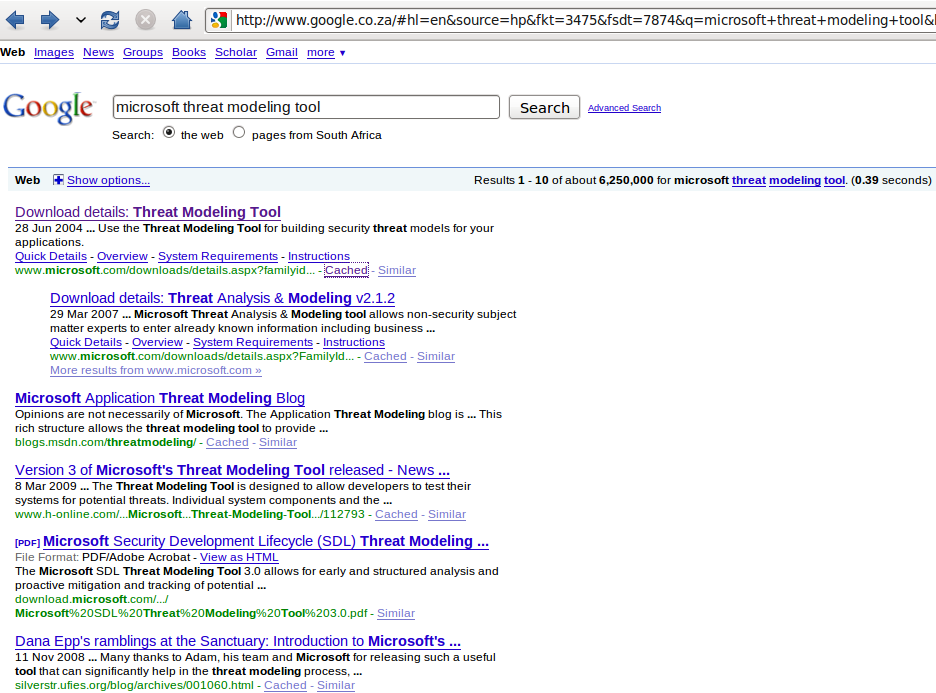
A subsequent Google for the Microsoft Threat Modeling (sic) Tool this morning, provides the following…
The first link is the package we’re looking for. Clicking on the Cached page, we get:
Clicking on the “really-real” link, we get the following…
/ian